Picture this: you’re the mastermind behind a flourishing MLM business, utilizing cutting-edge MLM software to streamline your operations and maximize growth. But amidst the zest of success, have you ever paused to ponder why data security is vital for MLM software?
As the world becomes increasingly interconnected and cyber threats grow more sophisticated, the need for robust data security measures within MLM software has become even more critical. Multi Level Marketing businesses rely heavily on managing vast amounts of sensitive data, including customer details, payment information, sales records, and organizational structures.
In this article, we will explore the importance of data security for MLM software, considering the current technological landscape and the potential risks associated with data breaches. So get ready to board your flight ✈️
What is Data Security?
Data security is the process of protecting digital information from unauthorized access, corruption, and theft at every stage of its existence. It is the measures taken to ensure that digital data remains secure and inaccessible to unauthorized entities.
MLM software has emerged as the cornerstone that supports and facilitates various business activities and transactions. In this context, data security becomes an indispensable aspect of MLM software, as it plays a pivotal role in safeguarding sensitive information. Consequently, selecting the most suitable MLM software is a top priority to ensure the protection and integrity of valuable data.
Why is it Important for MLM Software?
As we all know, multi-level marketing is usually based on product sales, relying on e-commerce practices to drive sales and propel business growth.
So the MLM companies and the integrated E-commerce platform need to meet the security standards for storing and maintaining the customer’s data, all the financial transaction data, and all the MLM related data.
However, this dependence on digital platforms also exposes MLM businesses to a myriad of risks, making data security an imperative aspect of their operations. Just consider the staggering amount of sensitive information involved in MLM activities: from processing orders and credit card payments to storing and managing user data.
As these data are more prone to fraudulent activities, they should always be stored in an encrypted format, and it is good to avoid storing data in plain format. Multi level marketing also involves storage requirements like storing the distributors’ data, downlines, commission plans, and payment details.
For instance, a group of hackers attempted to steal $24 million from a multi-level marketing (MLM) business by taking advantage of a weakness in their IT system. Let’s look at more examples:
- International MLM firm Arbonne International exposed the personal information and credentials of thousands after its internal systems were breached by an unauthorized party. (Source:https://www.bleepingcomputer.com/news/security/arbonne-mlm-data-breach-exposes-user-passwords-personal-info/)
- InfoTrax Systems, a provider of back-end operations systems and an online distributor of MLM software for the Direct Sales industry, discovered the security compromise only after it had already occurred. According to the FTC press release, the hacker penetrated InfoTrax’s servers and websites maintained on behalf of the company’s clients more than 20 times between May 5, 2014, and March 7, 2016, and had access to the servers for more than two years. (Source:https://www.bleepingcomputer.com/news/security/infotrax-gets-slap-on-the-wrist-after-being-breached-20-times/)
These real-world examples emphasize the urgency for MLM companies and integrated e-commerce platforms to uphold security standards. Implementing cutting-edge encryption technologies, access controls, and comprehensive data protection protocols is no longer optional but vital to reinforce the MLM ecosystem against the relentless onslaught of cyber threats.
Different Types of Data Security for Enhanced Protection
Encryption
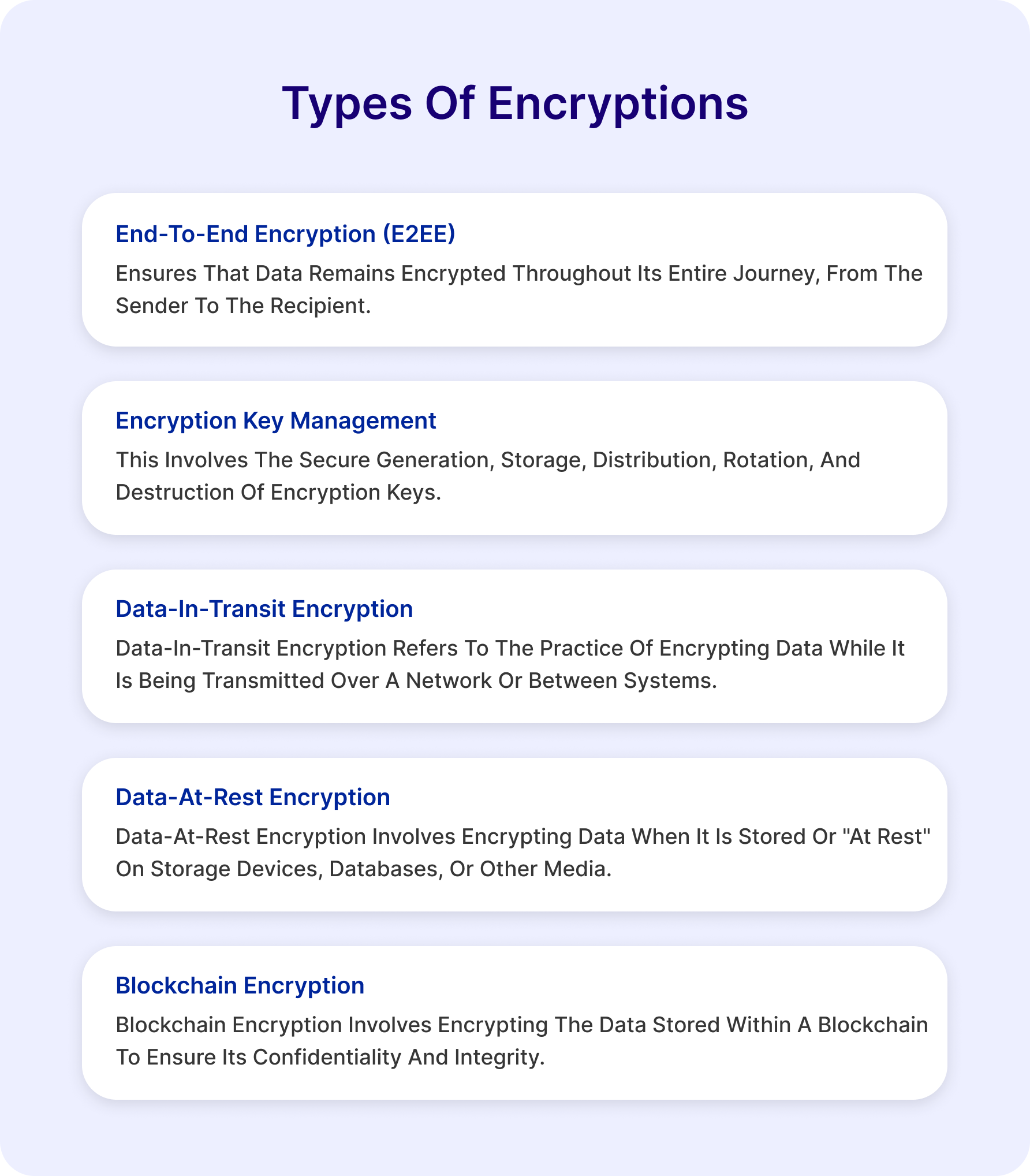
Encryption plays a crucial role in a direct selling business, especially when dealing with a significant amount of distributor and customer information. By employing encryption, only authorized users with the appropriate corresponding keys can access this sensitive information. It acts as a robust safeguard, creating a final line of defence for all incoming and outgoing data within an organization. There are many types of encryption used to secure data like: End-to-end encryption, Encryption Key Management, Data-in-Transit Encryption, Data-at-Rest Encryption, Blockchain Encryption, etc.
Authentication
Access to data crucial for an organization’s security and defence is granted to authorized individuals through various means such as passwords, PINs, biometrics, and security tokens. These authentication methods act as gateways, allowing only authorised individuals to access sensitive data.
Data Masking
To prevent data leakage from direct selling databases during potential breaches or hacking attempts, a technique is employed that temporarily masks personally identifiable information (PII) with proxy characters. This process ensures that unauthorized entities attempting to access the data cannot retrieve sensitive information, thereby providing additional protection for the PII stored in the databases.
Recovery and Backup
In the direct selling industry, the data security system should include provisions for backing up and recovering data copies from mitigating risks like system failures, data corruption, breaches, or disasters. These copies can be stored in various locations, such as physical disks, cloud storage, or the local network. By implementing a robust backup and recovery strategy, organizations can ensure the availability and integrity of their data, even in the event of unexpected incidents or emergencies.
Database Security Features of MLM Software
The basic security features of the MLM software that should be included are as follows:
- SSL (Secure Socket Layer ) Encryption
- PCI DSS-Payment Card Industry Data Security Standard
- IP (Internet Protocol) blocking
- DDoS- Denial Of Service
- Encryption of Database
- Encryption of Password
- Backup-Database
#1. SSL (Secure Socket Layer ) Encryption
SSL is Security based technology for maintaining the encrypted data via the link between the web browser and the webserver.
Host provider provides the SSL certificate and the same has to be installed for implementing SSL (Secure Socket Layer ) encryption.
Why SSL?
This encrypted link ensures data security and prevents unauthorized data access.
How to understand the website implemented SSL?
You can understand the same from the website address bar. The address indicates https:// in the address bar of the website. The website without SSL indicates http:// in the address bar of the website and it shows that it is an insecure website.
If the customer submits any of the data related to his credit card details, it means the data is transferred between the server and the client in the plain format and it is prone to unauthorized access or hacking.
#2. PCI DSS-Payment Card Industry Data Security Standard
The PCI DSS (Payment Card Industry Security Standard ) is a standard for the security required by all the suppliers of the credit card.
Card suppliers should be PCI compliant. This standard should be followed by all the organizations which process, store or transfer the cardholder details or data. So the MLM software and the websites must comply with PCI
PCI compliance is a process which is continuous and it is defined by the PCI Security Standards Council and the steps involved in the PCI compliance are as follows:
Access :-
To identify the security vulnerabilities, the defined business processes for processing the card and the list of the IT assets of the suppliers.
Remediation:-
Resizing the storage of cardholder data to confine what is required for storing to rectify and prevent the vulnerabilities
Reporting :-
The reports are compiled after regular security monitoring to obtain the card suppliers.
Why PCI?
Its main theme is to prevent fraudulent activities involved in this. PCI Security Standards Council administers the PCI standard. If anyone is not PCI compliant, you may lose eligibility to accept payments via credit card completely and also need to face the charged fine.
#3. IP Blocking
IP refers to Internet protocol, which is provided by the cloud service providers and the software.
Why IP Blocking?
This IP blocking service is used by the organization to block a group of people or the individual to access your website. IP blocking is important in case of data security, in case of any fraudulent activities monitored, the IP can be blocked. The same capability should be offered by your MLM software to block any IP or a range of IP’s
#4. DDoS-Denial Of Service
DDoS refers to a Distributed Denial Of Service Attack. It is a service attack and not the security feature.
Why DDoS to be taken care?
Any security feature to be included in your MLM software to prevent this cyber attack. This attack prevents the customers to access your website and it temporarily blocks the website access by increasing the illegal traffic to the websites.
This cyber will make the website to respond slowly due to illegitimate heavy traffic produced by hackers. Thus the MLM software should follow certain actions or plan to implement any security feature to overcome this DDoS attack.
#5. Encryption of Database
To prevent the data from being vulnerable to any malicious activities or fraudulent activities, your MLM software should implement strong encryption techniques.
NSA (National Security Administration) defines the rules and regulations to store the data of credit card.
Why Encryption of Database?
To avoid storing credit card data in the plain format, the encryption techniques will be useful. It should be taken care to store the security code of the credit card data in the encrypted format. Overall the database will be secured with encrypted data.
#6. Encryption of Password
In the MLM software, the password you enter in any part of the application should be in the encrypted format. Make sure that the software provider uses MD5 encryption technique to store the password in the encrypted format.
Why Encryption Of Password?
If the passwords are stored in the plain format, then it is more prone to hacking or any fraudulent activities to obtain unauthorized access to the accounts of the customer and the distributors. They can also be able to access the admin account where it affects the entire business operations.
#7. Backup-Database
Backup also falls under the security measures to be taken in your MLM software.
Why Backup-Database?
If the entire data related to your customers, distributors, commission payments, commission plan, merchant account, product details are lost, then it will affect your MLM business drastically.
To restore the data in case of any data loss, you need to have a backup of MLM software. MLM software should offer the daily or weekly backup of the data to avoid data loss.
Conclusion
Finally, in this article, you will be able to understand why data security is important for MLM software. Ensure that the MLM software provider is taking care of these security features and the same is implemented with the advanced encryption techniques to promote your MLM business more securely.
Data security is indispensable in MLM software to enhance the overall business productivity by securing the data of the customer and the organization. Wisely choose the MLM software provider to secure your customer and organization data of MLM business.